With over 200,000 banned Chinese surveillance devices still operating across America and sophisticated cyber threats targeting CCTV networks daily, network separation has become the most critical security measure for protecting your surveillance infrastructure. This comprehensive guide reveals why air-gapping your CCTV network from the internet isn't just best practice—it's essential for preventing devastating breaches that cost U.S. businesses $300 billion annually.
The Hidden Threat in Your Security Cameras
Your CCTV system might be your biggest security vulnerability. If you're using cameras from Hikvision, Dahua, Lorex, or dozens of other manufacturers with Chinese-made components, your surveillance network could be actively compromising your organization's security—even if you purchased them through reputable U.S. distributors.
The Scope of the Problem
Recent federal investigations have revealed alarming statistics:
- 60% of global IP cameras contain components from banned Chinese manufacturers
- 200,000+ Dahua devices and 15,000+ Hikvision cameras remain active in U.S. networks
- 82% of organizations have at least one vulnerable CCTV device connected to their network
- $45 billion in annual losses directly attributed to compromised surveillance systems
Understanding the NDAA Ban and Its Implications
Section 889: What You Need to Know
The National Defense Authorization Act (NDAA) Section 889, effective August 2019, prohibits federal agencies and contractors from using surveillance equipment from:
Primary Banned Manufacturers:
- Hikvision (Hangzhou Hikvision Digital Technology)
- Dahua (Dahua Technology Company)
- Huawei (Huawei Technologies Company)
- ZTE (ZTE Corporation)
- Hytera (Hytera Communications Corporation)
- Raysharp (Added October 2024)
The White-Label Problem
What makes this ban challenging is the widespread use of OEM (Original Equipment Manufacturer) partnerships. Many familiar brands are actually repackaged Chinese technology:
Common OEM Relationships:
- Lorex → Uses Dahua components
- Swann → Rebranded Hikvision
- LTS → Hikvision OEM
- Amcrest → Dahua technology
- Night Owl → Various Chinese manufacturers
- EZVIZ → Hikvision subsidiary
- LaView → Hikvision OEM
- Q-See → Mixed Chinese components
The Three Categories of CCTV Security Vulnerabilities
1. Intentional Backdoors ("Sponsored" Vulnerabilities)
Chinese law requires all companies to cooperate with intelligence gathering when requested. This has led to:
- Hardcoded credentials that cannot be changed
- Hidden administrative accounts accessible remotely
- Forced cloud connectivity routing through Chinese servers
- Firmware update mechanisms that can install malicious code
- Data exfiltration protocols disguised as telemetry
Real-World Example: In 2023, security researchers discovered Hikvision cameras automatically connecting to servers in China every 30 minutes, transmitting encrypted data packets even when cloud features were "disabled."
2. Unintentional Security Flaws
Poor security practices create additional vulnerabilities:
- Unencrypted data transmission exposing video feeds
- Weak default passwords (often "admin/12345")
- Outdated firmware with known exploits
- Open ports allowing unauthorized access
- Buffer overflow vulnerabilities enabling code execution
3. Supply Chain Compromises
Even non-Chinese branded cameras may contain compromised components:
- Huawei HiSilicon chips found in 40% of "secure" cameras
- Compromised firmware libraries shared across manufacturers
- Malicious code injected during manufacturing
- Hardware implants undetectable by software scans
The Consequences of Compromised CCTV Networks
For Your Business Operations
When attackers gain access through CCTV vulnerabilities, they can:
- Disable security monitoring during criminal activities
- Access live feeds to plan thefts or attacks
- Pivot to other systems using the camera network as entry point
- Launch ransomware attacks encrypting critical business data
- Steal intellectual property through network traversal
- Conduct espionage gathering competitive intelligence
Legal and Compliance Implications
Using banned equipment can result in:
- Loss of federal contracts worth millions
- $7,000 fines per unauthorized device
- Medicare/Medicaid exclusion for healthcare facilities
- Insurance claim denials for security breaches
- Liability lawsuits from compromised data
The Network Separation Solution: Your First Line of Defense
Why Network Separation Works
Network separation (air-gapping) creates an impenetrable barrier between your CCTV system and the internet, preventing:
- Remote exploitation of vulnerabilities
- Data exfiltration to foreign servers
- Malware propagation to business systems
- Unauthorized access from external attackers
- Command and control communication
Implementing Proper Network Segregation
❌ Commonly Used But Flawed Design (Minimal Security)
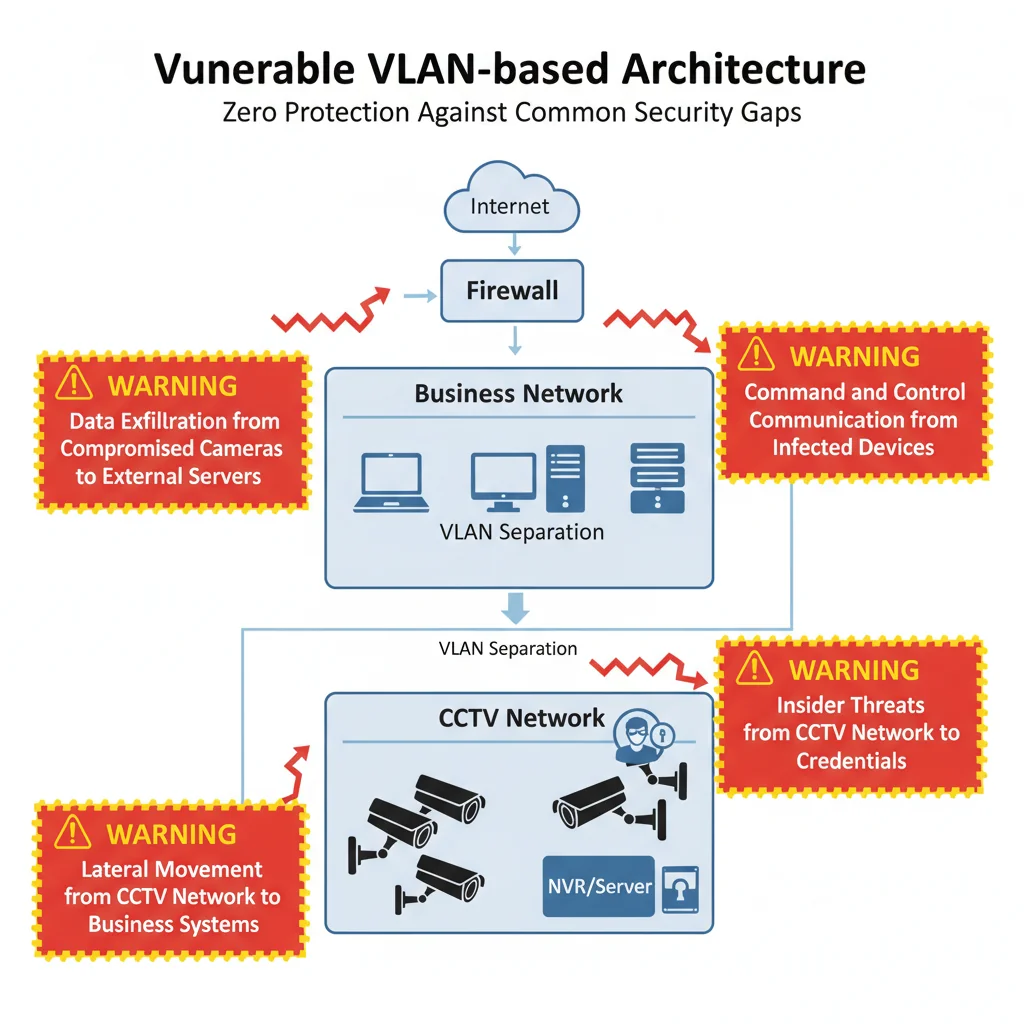
Critical Flaw: This design provides almost no security at all. In today's threat landscape, the majority of attacks come from inside networks, not outside. This commonly used architecture offers zero protection against:
- Data exfiltration from compromised cameras to external servers
- Command and control communication from infected devices
- Lateral movement from CCTV network to business systems
- Insider threats and compromised credentials
✅ Recommended Secure Architecture
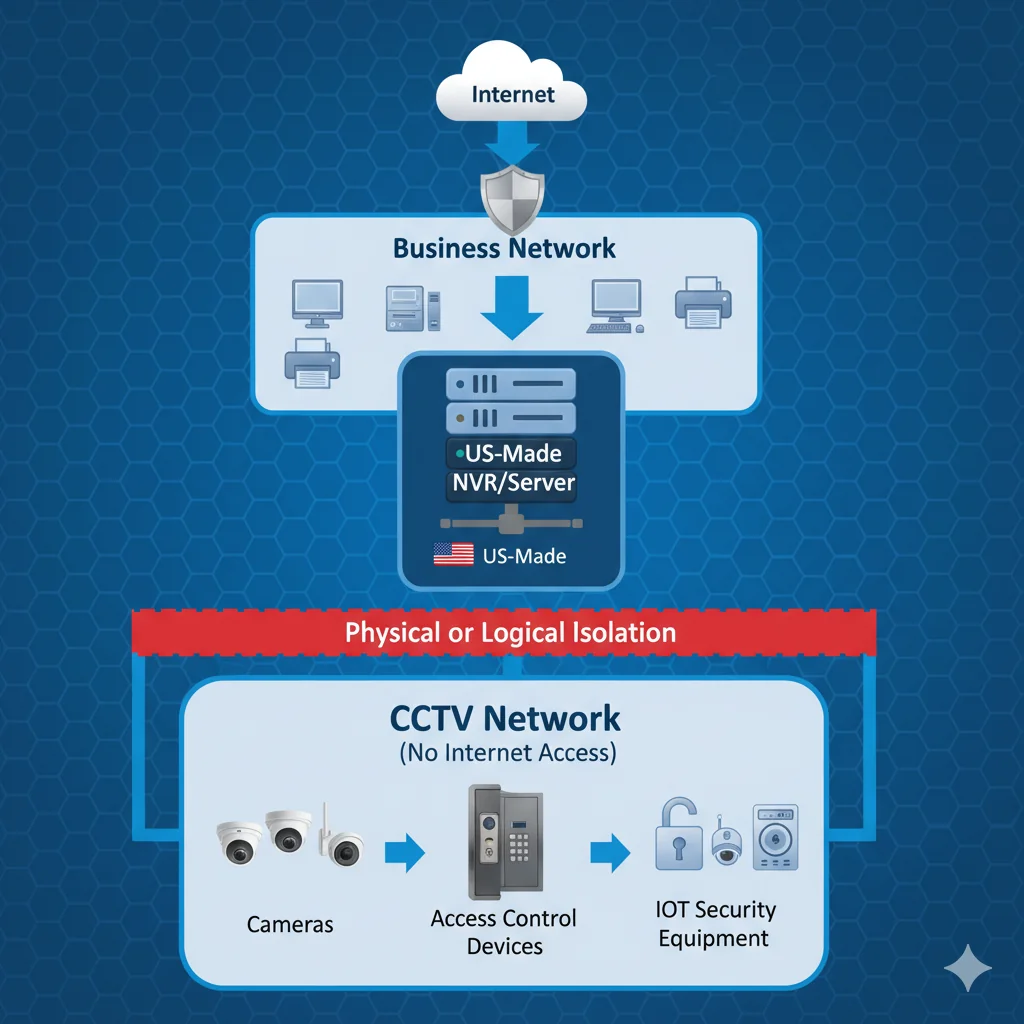
Why This Design Works:
This architecture positions the US-manufactured NVR/Server as a secure gateway between your business network and the isolated CCTV network. The NVR acts as a one-way valve—it can pull video from cameras but cameras cannot initiate connections outward.
Key Security Benefits:
- Complete Internet Isolation: Cameras have zero ability to communicate with external servers, preventing data exfiltration and "phone home" attempts
- Controlled Access Point: The US-made NVR serves as the only bridge, with strict firewall rules allowing only necessary protocols (RTSP, ONVIF) from NVR to cameras
- Maintained Usability: Unlike complete air-gapping, authorized users can still access video feeds through the NVR's business network interface
- Audit Trail: All access to camera feeds goes through the NVR, creating comprehensive logs
- No Lateral Movement: Even if a camera is compromised, it cannot reach business systems or the internet
Implementation Requirements:
- Dual-NIC NVR Configuration: One interface on business network, one on isolated CCTV network
- Strict Firewall Rules: Block all traffic from CCTV network except NVR-initiated connections
- VLAN Configuration: Cameras on separate VLAN with no routing to business network
- Disable Camera Cloud Features: Turn off all manufacturer cloud services, P2P, and DDNS
- Regular Security Audits: Monitor for unauthorized connection attempts
⚠️ Critical Implementation Notes
Physical vs. Logical Isolation: While physical isolation (separate switches, cabling) provides the highest security, properly configured logical separation with VLANs and firewall rules can achieve similar protection levels when physical separation isn't feasible.
NVR Selection is Critical: The entire security model depends on using a trustworthy, US-manufactured NVR without backdoors. Compromised NVRs defeat the entire security architecture.
Best Practices for Secure CCTV Network Design
1. Hardware Selection
Choose NDAA-Compliant Manufacturers:
- Axis Communications (Sweden)
- Pelco (USA)
- Bosch (Germany/USA)
- Hanwha Vision (South Korea)
- Verkada (USA)
2. Network Architecture
Physical Separation Requirements:
- Dedicated network switches for CCTV
- Separate network cabling (different color coding)
- Isolated power infrastructure
- Physical security for network equipment
Logical Separation (If Physical Not Possible):
- Implement strict VLANs with no inter-VLAN routing
- Deploy next-generation firewalls between networks
- Use jump boxes for administrative access
- Enable network access control (802.1X)
3. The Hidden Catch: Compromised NVRs
Many organizations implement network separation but overlook a critical vulnerability: their Network Video Recorder (NVR) or video management server may also be compromised.
Trusted NVR/VMS Providers:
- Milestone Systems (Denmark/USA)
- Genetec (Canada)
- Avigilon (Canada/USA)
- exacqVision (USA)
- S-VIDIA (USA)
Real-World Implementation Guide
Phase 1: Assessment (Week 1)
Inventory Current Equipment:
- Document all camera models and manufacturers
- Identify NVR/server specifications
- Map network topology
- Review firewall rules
Phase 2: Planning (Week 2-3)
Design Secure Architecture:
- Create network separation plan
- Specify compliant replacement equipment
- Develop implementation timeline
- Calculate budget requirements
Phase 3: Implementation (Week 4-6)
Network Preparation:
- Install dedicated CCTV switches
- Configure VLANs if required
- Implement firewall rules
- Set up monitoring systems
Phase 4: Validation (Week 7-8)
Security Testing:
- Penetration testing
- Vulnerability scanning
- Access control verification
- Incident response testing
Cost-Benefit Analysis
Investment Required
Small Business (10-20 cameras):
- Equipment replacement: $15,000-$30,000
- Network infrastructure: $5,000-$10,000
- Implementation: $5,000-$10,000
- Total: $25,000-$50,000
Medium Business (50-100 cameras):
- Equipment replacement: $75,000-$150,000
- Network infrastructure: $20,000-$40,000
- Implementation: $15,000-$30,000
- Total: $110,000-$220,000
Return on Investment
- Prevent average breach cost: $4.45 million
- Avoid NDAA non-compliance fines: $7,000 per device
- Maintain federal contract eligibility: Varies
- Reduce insurance premiums: 15-20% savings
- ROI: 300-500% within 3 years
Emergency Response: What to Do If You Have Banned Equipment
Immediate Actions (Within 24 Hours)
Isolate Affected Systems:
- Disconnect cameras from internet
- Disable remote access features
- Block outbound connections at firewall
- Document all equipment
Short-Term Mitigation (Within 7 Days)
Implement Network Separation:
- Create isolated VLAN for CCTV
- Deploy firewall rules blocking internet access
- Disable all cloud features
- Change all default passwords
Conclusion: Security Through Separation
The threat posed by compromised CCTV equipment is real, documented, and growing. With nation-state actors actively exploiting these vulnerabilities and cybercriminals launching increasingly sophisticated attacks, network separation isn't just a best practice—it's essential for survival in today's threat landscape.
By implementing proper network segregation, choosing NDAA-compliant equipment, and following security best practices, you can transform your CCTV system from a liability into a truly secure asset that protects rather than compromises your organization.
Remember: The cheapest camera system becomes the most expensive when it enables a multi-million dollar breach.
Take Action Today
Don't wait for a breach to discover your vulnerabilities. Contact CCTV Trailer for:
- Free Security Assessment of your current CCTV infrastructure
- NDAA Compliance Consultation to identify banned equipment
- Network Separation Design customized for your needs
- Deployment of Secure, US-Made surveillance solutions
- Same-Day Emergency Response for critical security needs
Contact Information
CCTV Trailer - Secure Surveillance Solutions
Phone: (253) 683-2288
Website: www.cctvtrailer.com
Emergency Response: Available 24/7
Related Articles
Why S-VIDIA's FDC Technology Revolutionizes Security
Learn about forensic-quality surveillance technology
True Cost of Construction Theft vs Security Investment
Data-driven analysis of theft losses and security ROI
Construction Security Compliance Guide
Meet OSHA and insurance requirements with mobile surveillance
Wireless Security Systems
Deploy secure surveillance without network vulnerabilities